Enterprise Mobile Management; MDM vs EMM vs UEM vs MTD vs MARS
MobileBack when I was a network administrator, mobile phones were only just starting to spread throughout the corporate world. Blackberry ruled the industry with their Blackberry Enterprise Suite, and the privileged few employees were issued with phones. For the most part however, mobile devices remained very much personal and with minimal access to corporate resources.
All that changed some years ago, and it’s quite common to see workers in the field with two phones; one business, and one personal. Yes you could combine them – but with businesses wanting to take control of not only the device, but the data it can access, combination means sacrifice. Do I yield control of my own handset over to IT? I think not!
So issuing phones still makes sense. But how do you protect what will likely become the largest attack surface by far in coming years?
First, there was the MDM
Mobile Device Management became a thing. Being able rein in the handset was an absolute must. Companies like AirWatch and MobileIron started popping up to solve this very problem, ensuring network administrators could track\lock devices, remotely wipe contents and even control the applications available to be installed. Always-on VPN’s could be established to ensure corporate firewalls\proxies remained in effect.
Gartner redefines to EMM
As the mobile market matured, and applications became smarter, more abundant and feature-rich, it became apparent that protection of the handset alone wasn’t enough. The 2010’s onwards saw a surge in cloud application adoption, resulting in not only requiring protection for a device, but for the data it was accessing too.
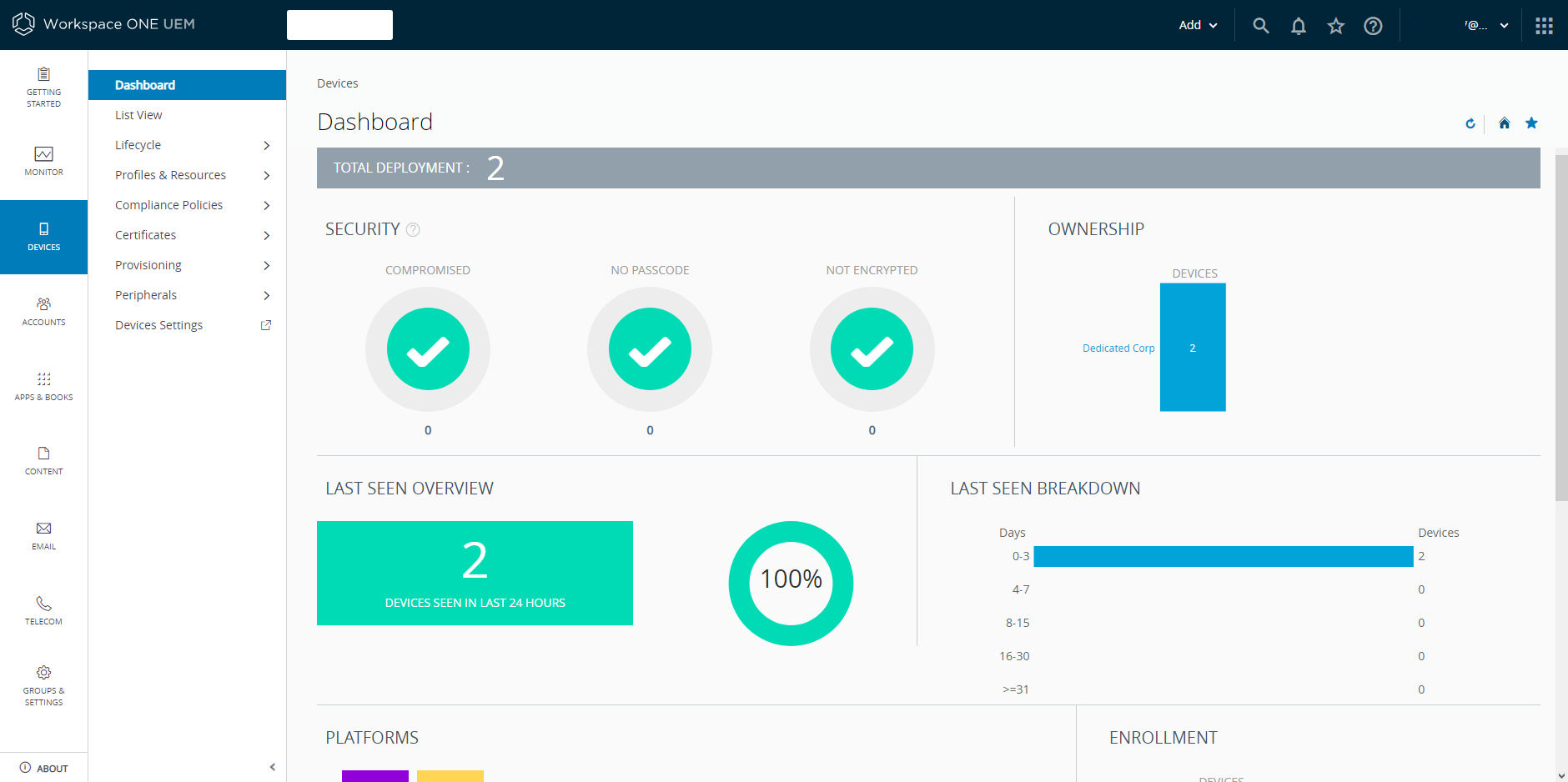
Enterprise Mobility Management provided never-before seen controls for mobile such as DLP and cloud based directory services integration (think Azure AD and Okta). MDM was no longer a term which described the array of controls provided by EMM, which covered not only the device, but the user too.
Think bigger, UEM
But why stop there? Mobile management was just one part of an organisations battle to control anything with an IP address. Unified Endpoint Management expanded to Internet of Things (IoT), printers, kiosks, tablets and a host of other ‘mobile-like’ devices.
Mobile gets ugly; Mobile Threat Defence & MARS
It never takes long until a new digital platform becomes weaponised. IoT went thought it, and while mobile largely escaped without catastrophe, it wasn’t without its threats.
Queue a plethora of start-ups aimed at protecting the mobile industry. While many argue it strictly isn’t necessary (thanks the seemingly good work Apple and Google do at protecting their respective operating systems) – there are still cases of monumentally stupid applications being authorised in the stores of both camps.
Regardless of whether malware made it into the store or not, sideloaded apps via jailbroken devices was an easy win for malware authors, and malware families such as Golduck affected iPhones, and Gustuff on Android. Infections from malicious USB chargers, rouge developer certificates and man-in-the-middle attacks all are very real threats today, affecting both iOS and Android equally (though some attacks are harder than others across the different platforms).
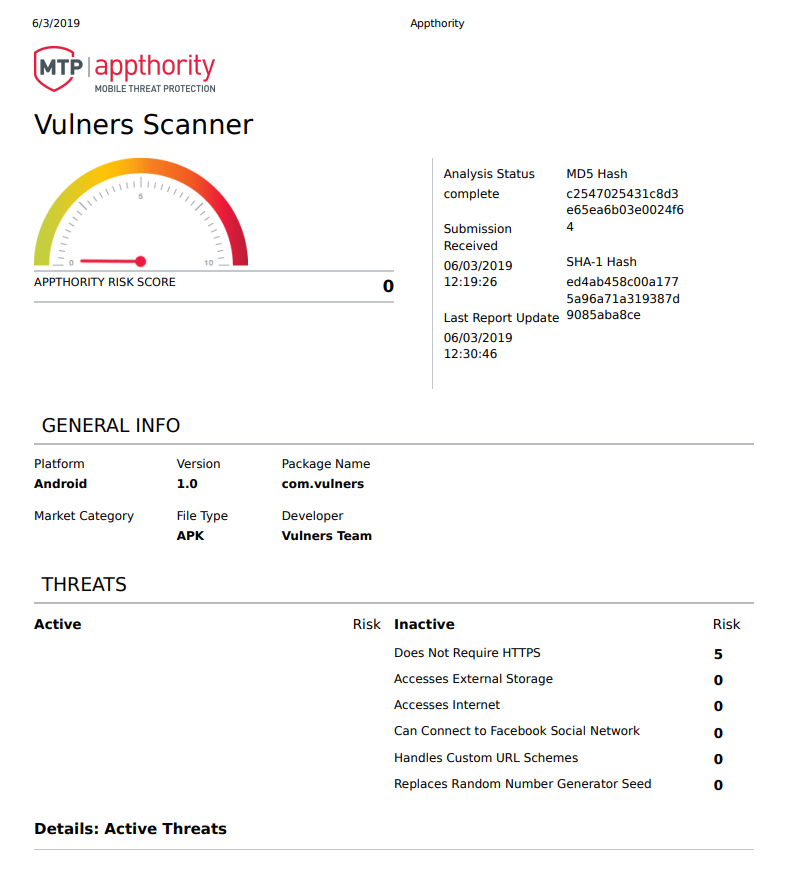
Finally, because of the sheer amount of crap applications being posted to Google Play and iTunes stores, it was clear that a reputation based system (beyond what Google and Apple were doing) may alleviate the problem. It can’t hurt to get a second opinion, right?
Appthority, Zimperium and Wandera are all examples of these latest tools in Mobile Threat Defence (MTD), and Mobile Application Reputation Service (MARS). We’ve come a long way in a very short time from the world of simple MDM’s, and if you’re serious about monitoring corporate mobile security, I’d strongly recommend looking at what the industry has to offer in the MTD space.
