Exploit attempts - Yearly roundup
InfosecIt’s always interesting to look through The Serpent’s logs to see what unusual traffic makes its way to our doors. If 2020 has taught us anything, it’s that the names of exploits may change, but the methods have largely remained the same.
The site has been online for over 20 years now, and therefore gets a decent share of bot traffic, but also we see a constant attempt to exploit web technologies commonly used throughout the Internet. I thought I’d share some of the top reconnaissance events, in order to give our readers an insight into what personal websites experience these days.
PHP still king
The most common exploit attempts focused on PHP attacks. The Serpent dropped PHP years ago for this very reason. Despite being a language that will always have a place in my heart, we got hacked too many times so it had to go. That still doesn’t stop the attempts coming in however:
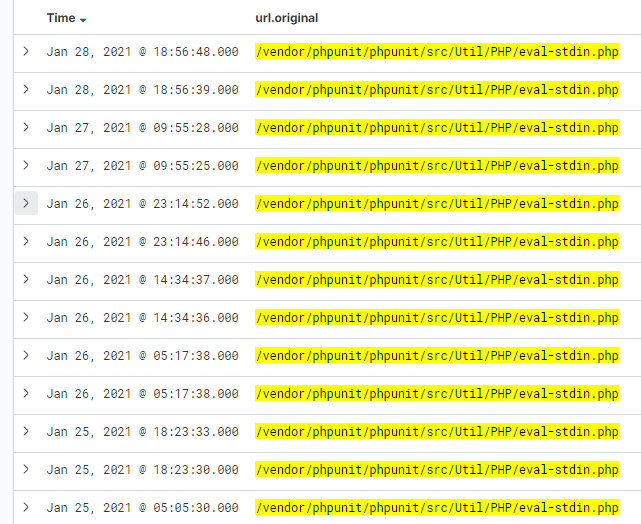
As you can see, there’s a handful of attempts per day, totalling hundreds of attempts per month (around 500 just for this particular exploit alone). The exploit in question is CVE-2017-9841, which affects a framework library called PHPUnit. For a four year old exploit, it’s still generating a lot of traffic.
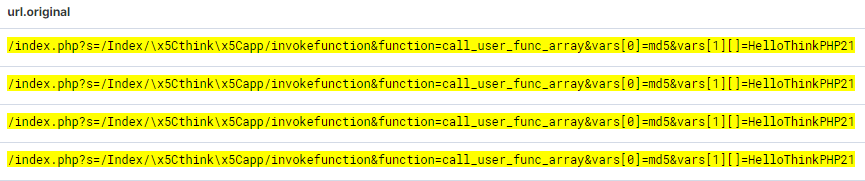
The other most common PHP attack of 2021 was ThinkPHP. At its peak it generated about 1,000 hits a month. Fortunately it’s very easy to spot:
Wordpress Woes
A close second on the list of attacks over the last year was Wordpress. A popular Content Management System (written in PHP), it’s had its fair share of exploits. Standard recon techniques attempt to find the login portal, or left over configuration files which are readable:
Fortunately, there’s no wp-login.php here.
Directory Traversal FTW
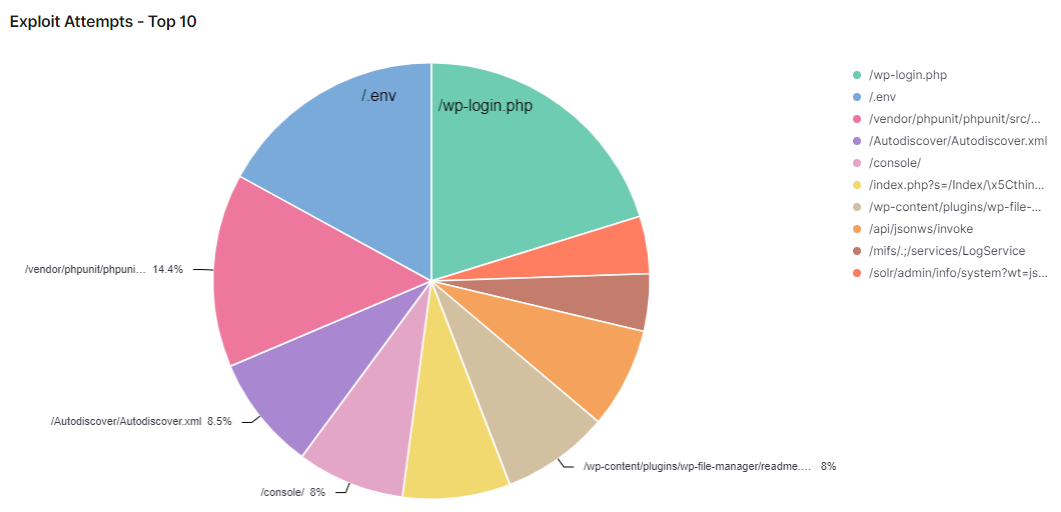
The most worrying attacks go after the web server directly. The chart above show that directory traversal attacks were a close third place. Web Server exploits don’t come up as often, but they are certainly more likely to let an attacker inside if successfully exploited. For this reason, the web server should always be ran with the lowest possible access rights and updated frequently.
The examples in the chart don’t always require an exploit. A poorly configured web server will provide the contents of files outside of its root directly if allowed. Therefore it’s always wise to spend time reviewing and refining web server configuration on a routine basis.
Good ol’ fashioned distruption
Lastly, there’s still plenty of noise being made by bots, port scanners and plain crazy internet users who just want to watch the world burn. The struggle to serve pages while ignoring requests that eat up resources is a difficult one, but one that we win more than we loose.
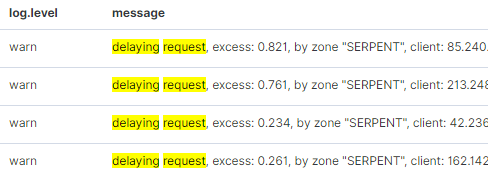
The DDoS attacks tend to come once a year, but rarely feel targeted. They are usually performed by aggressive search engine bots, which once blocked - leave us alone for another year.
